Basic Introduction
Reliability and peak performance are critical in the dynamic world of online services and apps. The necessity for effective task allocation is more pressing as traffic levels rise and user expectations rise. Let me introduce the load balancer, the unsung hero of contemporary IT architecture. We'll go deep into the realm of load balancers in this extensive tutorial, covering their significance, varieties, features, and best practices. Ensuring smooth speed and availability is crucial in the dynamic world of modern computing, where websites and applications serve millions of people concurrently. Behind the scenes, load balancers perform the unsung hero role of distributing traffic among servers in order to maximize resource usage, improve scalability, and strengthen dependability.
What is Load Balancer?
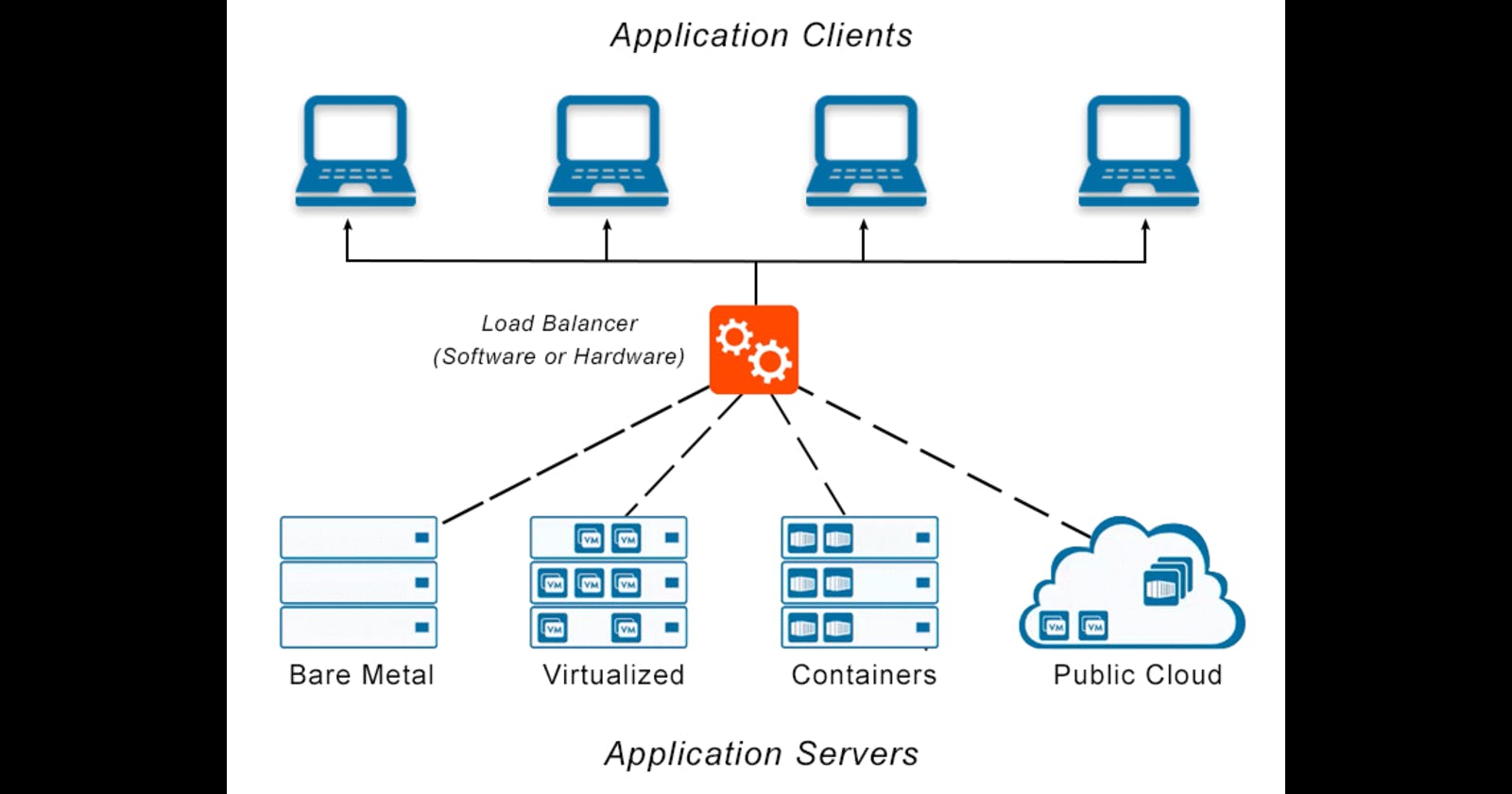
A load balancer is a one sort of tool or piece of software that spreads incoming network traffic among several servers or resources is called a load balancer. The main goal is to minimize bottlenecks and maximize resource usage by making sure that no single server is overloaded with requests. In their capacity as go-betweens, load balancers automatically route traffic according to preset criteria and algorithms.
Basically, a load balancer is a networking hardware or software program that divides incoming network traffic across several servers or resources in an equal manner. Load balancers stop any one server from being overloaded by effectively dispersing workloads; this prevents performance deterioration and possible outages. High availability and flawless performance are necessities in today's digital world, where internet services and apps form the foundation of many companies and sectors. In this situation, load balancers become the unsung heroes of contemporary IT architecture.
In order to effectively distribute incoming network traffic among several backend resources, including servers, virtual machines, and containers, a load balancer is an essential component that resides between clients and servers. Its main goal is to keep no one resource from being overloaded with requests, which maximizes resource use and guarantees peak performance.
In situations where sustaining uptime is crucial or where traffic quantities change unexpectedly, the significance of load balancers cannot be emphasized. Using pre-established methods and criteria, load balancers intelligently route traffic to assist businesses in achieving a number of important goals such as:
Security: In addition to serving as a barrier between clients and servers, load balancers may also improve security by putting in place access restrictions, SSL termination, and other security measures to guard against a variety of threats, such as DDoS assaults and unauthorized access.
Higher Availability: By splitting up traffic among several backend servers, load balancers are essential in guaranteeing high availability. Load balancers minimise downtime and preserve service continuity by smoothly rerouting traffic to healthy servers in the case of a server breakdown or maintenance.
Optimization in the Performance: Load balancers assist minimize bottlenecks and overloads by spreading incoming requests evenly among backend resources. This leads to faster response times and a better user experience.
Scalability: With the help of load balancers, businesses can easily expand their infrastructure to meet increasing traffic demands. Load balancers guarantee that resources are effectively used and that performance is high regardless of anticipated growth or an unexpected spike in users.
Moreover, we can say that the load balancers play a vital resource for any business looking to improve the performance, scalability, and dependability of its online services and applications. Load balancers are an essential part of contemporary IT infrastructure, enabling companies to adapt to the always changing needs of the digital world, whether they are implemented as software programs, hardware appliances, or cloud services.
Types of Load Balancers?
Cloud-Based Load balancers: For their specific platforms, cloud service providers provide load balancing solutions. These cloud services ease deployment and maintenance because they are completely managed and connect with other services effortlessly. Amazon Elastic Load Balancing (ELB), Google Cloud Load Balancing, and Azure Load Balancer are a few examples.
Software-Based Load Balancers: These load balancers function as regular applications on virtual or ordinary servers. They operate well in cloud settings and software-defined networking (SDN) configurations because of their flexibility and scalability. Nginx, mod_proxy_balancer in Apache, and HAProxy are well-known examples.
Hardware-Based Load Balancers: The Hardware load balancers are appliances made specifically for the purpose of load balancing. When managing large traffic loads, hardware load balancers are frequently chosen due to their excellent performance. Application-layer inspection and SSL offloading are examples of sophisticated functionality that they usually include.
Purpose of Load Balancers?
Security: In addition to serving as a barrier between clients and servers, load balancers may also improve security by putting in place access restrictions, SSL termination, and other security measures to guard against a variety of threats, such as DDoS assaults and unauthorized access.
Higher Scalability: Provide horizontal scalability by smoothly adding and deleting servers in response to demand. As traffic patterns change, make it easier for auto-scaling settings to dynamically modify resources.
Health Monitoring: Make sure that the backend servers are always in good condition and are available. To avoid sending requests to servers that are broken or overloaded, automatically eliminate unhealthy servers from the pool of accessible resources.
Traffic Distribution: Several servers or resources are equally distributed with incoming requests using load balancers. Choose the best destination for each request by utilizing a variety of techniques, such as IP hash, least connections, round-robin, etc.
Durability during the Session: In order to guarantee that a client's following requests are sent to the same backend server, it is necessary to maintain session affinity crucial for apps that need session-based authentication or stateful interactions.
SSL Termination: Transfer responsibility for SSL/TLS encryption and decryption from client servers to the load balancer. Lowering of the computational load on application servers will improve security and performance.
Content-based Routing: The Smart traffic routing may be achieved by load balancers using content-based routing, which takes into account headers, cookies, and URL routes. This allows for advanced traffic control plans that are adapted to the demands of certain applications.
Some best methods for Deploying Load Balancers
Security: Encrypt your data, apply access limits, and conduct frequent security audits to keep your load balancers safe. Utilize traffic filtering and rate limitation to defend against typical dangers like DDoS assaults.
Scalability: Select a load balancing system with horizontal scalability to meet increasing traffic needs. Make sure the solution you select can be readily extended as required and connects effectively with your current infrastructure.
Analytics and Monitoring: Make use of monitoring tools to keep an eye on important performance indicators including error rates, latency, and throughput. Examine this data to pinpoint areas of poor performance and adjust load balancer settings accordingly.
Consistency: To provide high availability, use redundancy and failover techniques. To reduce the possibility of single points of failure, distribute load balancers throughout several geographic locations or availability zones.
Considerations regarding the Load Balancer Deployment
The strategic choice of deploying load balancers is essential to guaranteeing applications' best possible performance, scalability, and security. Here is a thorough examination of important deployment tactics and considerations:
Security Factors to Consider: To protect client-server communication, put encryption techniques and access restrictions in place. Update the firmware and security fixes on load balancers on a regular basis to handle new threats and vulnerabilities.
Updating and maintaining on a regular basis:
Configuration audits: Perform regular configuration audits to make sure that security standards and best practices are being followed. Find and fix any potential security flaws or misconfigurations.
Firmware and Security Patches: Security patches and firmware updates should be applied on a regular basis to load balancers in order to patch vulnerabilities and counter new threats.
Security and Encryption Measures:
Methods of Encryption: Secure client-server communication may be achieved by utilizing encryption protocols like SSL/TLS, which protect confidential information from illegal access or modification.
Usage of Access Control Lists (ACLs): Use access control lists (ACLs) to restrict access to load balancers, enabling only systems or users that are permitted to do so.
Higher Availability and Redundancy: To reduce the possibility of single points of failure, use redundant load balancers. To guarantee continuous availability and smooth failover in the event of hardware or software problems, configure active-passive or active-active failover techniques.
Mechanisms for failure overflow:
Automatic Redundancy: The configuration of automatic failover techniques can provide a smooth transition in the event of hardware or software failures, therefore reducing downtime and guaranteeing continuous availability.
Regular Health Checks and Monitoring: To proactively identify faults and initiate failover operations, it is recommended to establish comprehensive health checks and monitoring systems.
The redundancy of load balancers:
Setup for Active-Active System: The utilization of active-active setups improves fault tolerance and scalability by distributing traffic among several active load balancers.
Setting Up an Active-Passive System: Configuring an active-passive redundancy system means that, in the event that the primary load balancer fails, a backup load balancer is prepared to take over and provide high availability.
On-Premises vs Cloud Load Balancers: On-premises load balancers are installed in a company's data center, giving it total control over network and infrastructure setup. The Cloud load balancers enable scalability, flexibility, and integration with other cloud services. They are offered by cloud providers as managed services.
A cloud-based load balancer:
Scalability and Flexibility: Cloud load balancers allow for the dynamic adjustment of resources in response to traffic needs. They are available as managed services from cloud providers.
Cost-Effectiveness: Pay-as-you-go cloud load balancers eliminate upfront hardware expenditures and provide cost-effectiveness, particularly for workloads that fluctuate.
Load balancers installed on-site:
Control and Customization: Organizations may customize setups to meet their unique needs thanks to the total control that on-premises load balancers provide over infrastructure and network setup.
Compliance with Data Sovereignty standards: On-premises deployment offers more confidence regarding data residency and regulatory compliance for enterprises subject to stringent data sovereignty standards.
Conclusion
In conclusion, the load balancers are essential components of contemporary IT infrastructure that help businesses develop online services and applications with high levels of performance, scalability, and dependability. Load balancers reduce downtime, avoid overloads, and improve user experience by selectively allocating incoming traffic across several servers. In today's digital age, load balancers are essential tools for maximizing resource utilization and guaranteeing flawless performance, whether they are implemented as software programs, hardware appliances, or cloud services. Basically, the Load balancers play a crucial role in modern IT infrastructure by improving scalability, bolstering dependability, and optimizing performance. Load balancers are essential for reliable application delivery and flawless user experiences, regardless of whether they are installed on-site or in the cloud. Through an understanding of load balancer kinds, functionality, and deployment concerns, companies can design systems that are efficient, durable, and able to handle the demands of the modern digital world.